Ensuring the security of your Azure App Service is crucial for protecting your application and data. Here’s a comprehensive guide to help you implement the best security practices for your Azure App Service.
1. HTTPS Only
Enforcing HTTPS ensures that all communications between clients and your web app are encrypted. This encryption protects data in transit from eavesdropping and man-in-the-middle attacks. Enabling HTTPS also helps meet compliance requirements and build trust with your users by providing a secure browsing experience.
2. FTPS Only
FTPS (FTP Secure) encrypts the file transfer process, safeguarding your data during uploads and downloads. Using FTPS is essential for maintaining data integrity and confidentiality when transferring files to and from your Azure App Service. This is particularly important when handling sensitive or personal information.
3. Cross-Origin Resource Sharing (CORS) Configuration
Setting up CORS properly ensures that your web application only accepts requests from trusted domains. CORS is essential for controlling which domains can interact with your web application, helping to prevent unauthorized access and cross-site request forgery (CSRF) attacks.
- Access Control: Restricts resources to specific domains.
- Enhanced Security: Mitigates risks of CSRF attacks.
- Improved Data Integrity: Ensures only authorized domains can interact with your app.
Refer to the Host a RESTful API with CORS in Azure App Service tutorial for more information.
Note that you can also handle CORS requests in your application. Please refer to the Microsoft documentation “App Service CORS vs. your CORS“. Better yet, use a service such as Cloudflare Workers to handle CORS without evening sending requests to your origin (App Service).
4. Securing Inbound Traffic with a Web Application Firewall (WAF)
Protecting your web app from common web vulnerabilities and attacks is essential. Implementing a Web Application Firewall (WAF) using services like Cloudflare or Azure Front Door can help mitigate threats such as SQL injection, cross-site scripting (XSS), and DDoS attacks. A WAF acts as a shield, inspecting incoming traffic and blocking malicious requests before they reach your application.
- Protection Against Common Attacks: Filters out malicious traffic.
- Improved Security Posture: Helps meet security compliance requirements.
- DDoS Mitigation: Protects against distributed denial-of-service attacks.
Network Access Controls: Use network access controls such as headers, service tags, and inbound IP addresses to prevent users from bypassing the WAF. This ensures that all traffic is inspected and filtered appropriately before reaching your application.
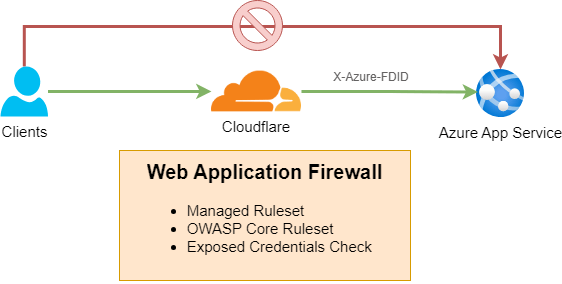
Refer to the Azure App Service Security: WAF Setup post for more information.
5. Managed Identity Instead of Credentials in Connection Strings
Using a Managed Identity for your Azure App Service is a more secure alternative to storing credentials in connection strings, even if they are securely stored in services like Azure Key Vault. Managed Identities provide an automatically managed identity in Entra ID for your app, which can be used to authenticate to any service that supports Entra ID authentication. This eliminates the need to manage credentials (usernames and passwords) and reduces the risk of credential leakage.
- Eliminates Credential Management: No need to store or manage credentials.
- Enhanced Security: Reduces the risk of credentials being exposed.
- Simplified Access: Easily grants access to Azure resources using RBAC (Role-Based Access Control).
6. Storing Secrets in Azure Key Vault
Azure Key Vault is a cloud service that provides secure storage for secrets, such as API keys, passwords, and certificates. Instead of using app settings to store these secrets, leveraging Azure Key Vault enhances security by centralizing and protecting sensitive information.
- Centralized Management: Securely store and manage secrets in one place.
- Access Control: Use Azure Active Directory to control access to secrets.
- Monitoring and Logging: Track and log access to secrets for auditing purposes.
7. Regular Security Updates for your Application Code
Keeping your application software updated with the latest security patches is crucial for protecting against known vulnerabilities. Regular updates help mitigate the risk of exploitation by attackers. This includes updating third-party dependencies such as NPM packages and NuGet packages. The latest versions of these packages often include bug fixes, performance enhancements, and, most importantly, security updates.
- Protection Against Exploits: Addresses known vulnerabilities.
- Improved Stability: Ensures your app runs on the latest, most secure versions.
- Compliance: Helps meet security and compliance standards.
8. Private Endpoints
Using private endpoints allows your Azure App Service to access resources such as databases, storage accounts, Redis Cache and Azure Key Vault over a private network connection rather than a public internet connection. This significantly improves the security of downstream resources by ensuring that traffic remains within the Azure network.
- Enhanced Security: Protects resources from exposure to the public internet.
- Improved Performance: Reduces latency by using private network connections.
- Compliance: Helps meet security and compliance requirements for network isolation.
9. Access Controls and Role-Based Access Control (RBAC)
Implementing RBAC helps manage who has access to your Azure resources. By assigning appropriate roles to users, you can ensure that only authorized personnel have access to sensitive areas of your application and infrastructure. Make sure the users managing the application and the managed identity are following the principle of least access, granting only the permissions necessary for their roles.
- Granular Access Control: Provides detailed control over user permissions.
- Enhanced Security: Minimizes the risk of unauthorized access.
- Auditability: Tracks and logs access changes for auditing purposes.
10. Infrastructure as Code (IaC)
Instead of making changes directly in the Azure portal, it’s recommended to use Infrastructure as Code (IaC) to manage your Azure App Service. IaC allows you to define your infrastructure in code, which can be version-controlled, peer-reviewed, and automated. This approach ensures consistency, repeatability, and traceability of changes.
- Trackability: All changes are recorded in version control.
- Peer Reviews: Promotes good practices such as peer reviews prior to making changes.
- Consistency: Ensures infrastructure is defined and deployed consistently.
11. Continuous Integration and Continuous Deployment (CI/CD)
Refrain from allowing users to deploy directly from their machines to Azure App Service. Instead, use CI/CD pipelines to release software. CI/CD pipelines automate the build, test, and deployment process, ensuring that only tested and verified code is deployed. This enhances security by incorporating practices such as vulnerability scanning and automated testing into the deployment process.
- Automation: Streamlines the deployment process and reduces human error.
- Security: Enhances the build with vulnerability scanning and automated tests.
- Consistency: Ensures that all deployments follow a standardized process.
12. Client Certificates Enabled
Enabling client certificates enhances security by allowing your web app to verify the identity of clients requesting access. This is particularly useful for scenarios involving sensitive data exchanges or requiring strict access controls. Client certificates add an additional layer of security by ensuring that only authorized clients can communicate with your app.
13. Session Affinity
ARR Affinity, or sticky sessions, should be enabled only if necessary (e.g., for in-process sessions). Disabling it when not needed improves load distribution across your instances, enhancing performance and scalability. For security, it’s important to understand when session affinity is required and when it can be safely turned off to avoid potential security risks associated with session handling.
14. Auto-Heal
Custom Auto-Heal policies can help maintain high availability by automatically recovering from unexpected issues. This ensures minimal downtime and quick recovery, which is essential for production environments. Auto-Heal can restart your app or perform custom actions when certain conditions are met, helping to mitigate potential security vulnerabilities caused by application errors.
15. Application Performance Monitoring
Application Performance Monitoring (APM) (e.g. Application Insights, Datadog etc) provides valuable insights into your app’s performance and health. It helps in diagnosing issues, monitoring performance, and gaining a deep understanding of user behavior. From a security perspective, APM can help detect anomalies and potential security incidents by monitoring and analyzing application logs and performance metrics.
Conclusion
Securing your Azure App Service involves a multi-layered approach, covering everything from secure communications to proper identity management. By following these best practices, you can create a robust security framework that helps protect your web applications from a variety of threats while ensuring compliance and trustworthiness